What is Ransomware?
On 12th May 2017, we saw what can be considered the biggest cyber attack in the Internet history. A Ransomware by the name of ‘WannaCry’ took the web by storm, creating damage with the epicenter in Europe. ‘WannaCry’ leveraged on a security vulnerability in the Windows OS, and infected computers. It just took the first few hours to infect more than 200,000 computers. Reports have it that it infected more than 99 countries, including Russia and China.
So what is Ransomware and why is it so damaging?
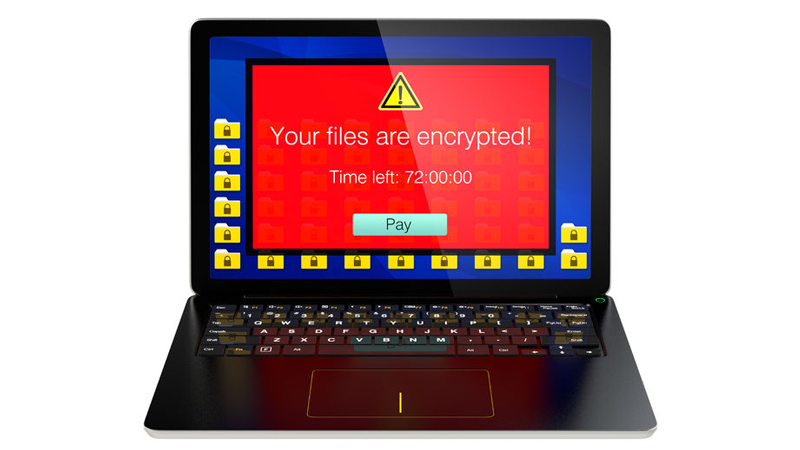
Ransomware is a type of Trojan cyberware that is designed to extort money from a victim. As implied by the name, Ransomware will demand a ransom or a payment (with a time limit) in order to undo the changes that the Trojan virus has made to the victim’s computer. These changes may include:
- Encryptors – Encrypting data that is stored on the victim’s computer so that information from the computer can no longer by accessed; and/or
- Lockers – Blocking access to the victim’s computer.
How does Ransomware Spread?
The attacker simply looks for the easiest way to infect a system or network, thereafter using this backdoor to spread the malicious content. Below is a list of examples:
- Spam email campaigns that contain malicious links or attachments (for example, office documents, PDF, HTML, XML, database files, CAD documents);
- Security exploits in vulnerable software (for example, operating systems);
- Internet traffic being redirected to malicious websites;
- Legitimate websites that have malicious code, unknowingly being injected into their web-pages;
- Botnets (robots in the Internet);
- Malwares disguised as Advertisements;
- Links or documents sent via SMS or Whatsapp messages (when targeting mobile devices);
- Self-propagation (spread from one infected computer to another by exploiting the vulnerability in the computer’s operating system or software).
How to prevent from being infected with Ransomware?
- Back-up your files regularly and most importantly, keep a recent backup off-site (not connected to any network).
- Don’t enable Macros in your software, for example, Microsoft Office.
- Install document viewers in your mobile or computer devices so that you can only view the document and not edit.
- DO NOT open unsolicited attachments and always seek clarifications from the sender off-line.
- Always update the latest security patches in your computers and mobile devices.
- One of the weakest link is people, so, always train and retrain your employees in your business so that they are knowledgeable and aware of the implications.
- Segment the company network by separating the LAN and the WAN so that it cannot be easily introduced into the internal systems in the company.
- Enable file extensions so that you are able to easily spot the type of files being sent to you or being downloaded.
- Open JavaScript (.JS), HTML, XML files in a Notepad as it would not be able to run any malicious scripts and you would be able to examine the contents in the file.
- If you suspect that your computer or mobile device is infected, IMMEDIATELY disconnect your computer or device from the network, quarantining it.
- Filter EXE and ZIP files in your emails.
- Disable Remote Desktop Protocol (RDP) if you do not need the service as it is a Windows utility that allows others to access your desktop remotely.
Image Credit: cheskyw/123RF Stock Photo

wow, very good advice!
Thank you very much, Wei Wah. We are glad that it is helpful to you.